Data Protection Addendum
This Data Protection Addendum (“DPA”) supplements and is made a part of those certain Aegis General Terms and Conditions executed by Aegis Industrial Software Corporation (“Aegis”) and Customer (the “GTCs”), to which this DPA is incorporated by reference. Capitalized terms used in this DPA without definition have the meanings ascribed to them in the GTCs. In the event of any conflict between this DPA and the Agreement, the provisions of this DPA will control.
1. DEFINITIONS
In this DPA, the following terms have the meanings set out below:
1.1 “Data Protection Laws” means any Law relating to data security, data protection and/or privacy, in any jurisdiction applicable to a Party’s processing of Personal Data under the Agreement.
1.2 “Customer Personal Data” means Personal Data that is provided by or on behalf of Customer or is otherwise processed by Aegis in connection with the performance of the Offerings. Customer Personal Data does not include business contact information collected by Aegis for the purpose of establishing and maintaining the Customer relationship.
1.3 “Controller” means the entity that determines the purpose and means of the processing of Customer Personal Data.
1.4 “Individual” means an identified or identifiable person to whom Customer Personal Data relates.
1.5 “Offerings” means Products and Services provided to Customer pursuant to the Agreement.
1.6 “Personal Data” means any and all information that, by itself or in combination with other information, identifies, relates to, describes, is capable of being associated with, or could reasonably be linked, directly or indirectly, with an Individual household or that is regulated as personal data, personal information, personally identifiable information or otherwise under Data Protection Laws.
1.7 “Privacy Rights Request” means a request from an Individual seeking to exercise a right related to their Personal Data, either pursuant to Data Protection Laws or Customer’s privacy policy (including requests to exercise any right of access, deletion, correction, opt-out of certain disclosures, or restriction of processing).
1.8 “Processor” means the entity that processes Customer Personal Data on Controller's behalf.
1.9 “Subprocessor” means any and all persons or entities (excluding an employee of Aegis) appointed by or on behalf of Aegis to process Customer Personal Data in connection with the Agreement.
2. PROCESSING OF CUSTOMER PERSONAL DATA
2.1 Each Party shall ensure that its data processing activities that occur by or in connection the Agreement comply with Data Protection Laws, and with respect to Customer, any applicable employment agreements or notices. Customer represents and warrants (i) it has conducted adequate due diligence to determine its obligations under Data Protection Laws, (ii) it has, as required, provided all notices and obtained all consents for Customer’s processing (or Aegis’ processing on behalf of Customer) of Customer Personal Data, and (iii) Customer’s disclosure of Customer Personal Data to Aegis does not violate Data Protection Laws.
2.2 The Parties acknowledge that Aegis may process Customer Personal Data on behalf of Customer: (i) for provision and enhancement of the Offerings, (ii) pursuant to Customer’s instructions as set forth in the Agreement, including this DPA, and (iii) as required or permitted by Law. If any other processing is required by Law, Aegis will inform Customer of that legal requirement before commencing such processing, unless providing such information to Customer is legally prohibited. The Parties further acknowledge and agree that, with regard to the processing of Customer Personal Data in connection with the Offerings, Customer is the Controller and Aegis is a Processor. Further details of the processing are identified in Attachment 1.
2.3 Customer directs Aegis to process Customer Personal Data on behalf of Customer as necessary for the provision and enhancement of the Offerings, which may include:
2.3.1 providing access to the Offerings and user support to Customer’s employees and other designees;
2.3.2 process records and data created by Customer, including records created automatically, using the Offerings;
2.3.3 verifying or maintaining the quality or safety of the Offerings;
2.3.4 undertaking activities to improve, upgrade, or enhance the Offerings (or any related features or functionality related thereto);
2.3.5 detecting data security incidents or protecting against malicious, fraudulent, or illegal activity; and
2.3.6 complying with Law, including Data Protection Laws.
2.4 Aegis acknowledges that it is prohibited from:
2.4.1 selling or sharing (as such terms are defined under Data Protection Laws) any Customer Personal Data or using Customer Personal Data for targeted advertising;
2.4.2 retaining, using, processing, releasing, transferring, disclosing, communicating, or otherwise making available Customer Personal Data outside of the direct business relationship between the Parties or for any commercial purpose other than the purpose of providing the Offerings specified in the Agreement; and
2.4.3 combining Customer Personal Data with any and all data that Aegis receives outside the business relationship with Customer.
2.5 Aegis shall promptly notify Customer in writing if Aegis becomes aware of or believes that any processing instruction from Customer violates Data Protection Laws or is unable to comply with Data Protection Laws or its obligations under this DPA. Where necessary Aegis will cease processing (except for secure storage) until such time as Customer issues new lawful instructions which Aegis is able to comply with. Aegis shall not be liable to Customer under the Agreement for any failure to provide the Offerings until such time Customer issues new lawful instructions.
2.6 Aegis shall ensure that any person authorized to process Customer Personal Data is subject to legally binding obligations to keep the Customer Personal Data confidential, and that such person will only have access to Customer Personal Data to the extent necessary to perform their job functions.
2.7 Customer will not provide (or cause to be provided) any sensitive Personal Data (as defined by Data Protection Laws) to Aegis for processing under the Agreement, and Aegis shall have no liability whatsoever for sensitive data.
2.8 Customer Personal Data excludes Account Data. The Parties acknowledge that Aegis is controller of the Account Data, such as to (1) manage the relationship with Customer; (2) provision accounts and authenticate users; (3) carry out business operations such as accounting, invoicing and filing taxes; (4) prevent, detect and investigate suspected security incidents, fraud and other abuse or misuse of the Offerings; (5) comply with legal or regulatory obligations; and (6) as permitted by law. For purposes of this DPA, “Account Data” means Personal Data collected by Aegis to establish and maintain the business relationship with Customer, including name and contact information of individuals authorized by Customer to manage Customer’s relationship with Aegis and payment information.
3. SUBPROCESSING
3.1 Aegis may not disclose Customer Personal Data to any external party (unless otherwise required by Law), except that Customer hereby grants general written authorization to Aegis to appoint Subprocessors to perform specific processing activities on its behalf. Where Aegis engages a Subprocessor, Aegis shall:
3.1.1 impose, in writing, on that Subprocessor data protection obligations that are no less protective of Customer Personal Data as those imposed on Aegis under this DPA and that meet the requirements of Data Protection Laws; and
3.1.2 disclose to Subprocessors only the minimum amount of a necessary Customer Personal Data to provide the Offerings.
3.2 Customer approves those Subprocessors that Aegis has engaged as of the date of this DPA. Before engaging a new Subprocessor, Aegis shall notify Customer (which notice may be by electronic mail and/or posting notice on a portal to which Customer has access). Customer may object in writing to any additional or replacement Subprocessor on reasonable grounds related to data protection within five (5) calendar days after receipt of the notice. If Customer objects, Aegis will use commercially reasonable efforts to resolve the objection.
4. PRIVACY RIGHTS REQUESTS
4.1 In the event that Aegis receives a Privacy Rights Request, inquiry, notice, or complaint from an Individual relating to Customer Personal Data, Aegis shall promptly (and in any event within ten (10) calendar days) notify Customer of such Privacy Rights Request in writing. Aegis may respond to the Individual solely to direct the Individual to submit their Privacy Rights Request to Customer, unless otherwise required by Data Protection Laws.
4.2 To the extent Customer does not have the ability to address a Privacy Rights Request through self-service features available in the Offerings, Aegis shall, upon written request, provide reasonable assistance to Customer in responding to Privacy Rights Requests that relate to Customer Personal Data in Aegis’ possession. Any requests from Customer for assistance with responding to a Privacy Rights Request shall be submitted via email to [email protected]. Within twenty (20) calendar days of an email request from Customer as described above, Aegis shall, upon request: (i) provide information requested by Customer about Aegis’ use of the Customer Personal Data (including, but not limited to, the categories of Customer Personal Data that were collected and categories of Subprocessors to whom Aegis has disclosed the Customer Personal Data); (ii) provide the specific pieces of Customer Personal Data that Aegis maintains about the Individual; and (iii) honor any and all Privacy Rights Requests submitted by Customer. If specific pieces of Personal Data are requested, and if the Customer Personal Data is maintained in an electronic format, the Customer Personal Data shall be provided in a portable and readily usable format that allows the Individual to transmit the information to another entity without hindrance. Customer shall be responsible for verifying the identity of the Individual who has submitted a Privacy Rights Request.
5. THIRD-PARTY DEMANDS AND GOVERNMENT ACCESS
5.1 If Aegis receives a request to retain, disclose or otherwise process Customer Personal Data from any third party (“Third Party Request”) or otherwise becomes aware of any direct access to Customer Personal Data by a Government Entity (“Government Access”), Aegis shall, to the extent legally permitted, promptly notify Customer in writing and provide all relevant details of the Third Party Request or Government Access, provided, however, that Aegis shall not be required to waive any legal privileges or breach any confidentiality obligations in order to comply with this Section 5.1.
5.2 In the event Aegis is prohibited from providing the foregoing notice to Customer, Aegis shall, at Customer’s expense, use reasonable efforts to obtain a waiver of the prohibition to enable Aegis to communicate as much information to Customer as possible, as soon as possible.
5.3 To the extent Aegis is legally required to comply with any Third Party Request, Aegis shall disclose only the portion of Customer Personal Data that is required to be disclosed and use reasonable efforts to obtain assurances that such Customer Personal Data will be treated confidentially.
6. SECURITY
Aegis shall comply with the Information Security Requirements, as set forth as Attachment 2 to this DPA.
7. DATA PROTECTION IMPACT ASSESSMENT AND PRIOR CONSULTATION
Upon Customer’s written request, Aegis shall provide reasonable assistance and cooperation to Customer to enable Customer to meet its obligations in relation to data protection impact assessments, and prior consultations with any Government Entity, taking into account the nature of processing and the information available to Aegis.
8. DELETION OR RETURN OF CUSTOMER PERSONAL DATA
8.1 At the termination or expiration date of the Agreement, Aegis shall delete Customer Personal Data from Aegis’ systems, unless retention is required by Law or if such Customer Personal Data is archived in Aegis’ back-up systems. In such case of archived Customer Personal Data, Aegis will protect the Customer Personal Data from any further processing and will delete the Customer Personal Data in accordance with Aegis’ back-up policies. Upon written request, Aegis will certify to Customer that all copies of Customer Personal Data have been deleted in accordance with this Section 8.1.
8.2 The terms of this DPA shall apply for as long as Aegis maintains Customer Personal Data.
9. AUDIT RIGHTS
9.1 Upon written request during the Term of the Agreement, Aegis will make available to Customer information reasonably necessary to demonstrate compliance with this DPA, which efforts may include periodic audits (not to exceed one (1) audit in any twelve (12) month period. Such audit will be conducted by an independent auditor acceptable to both Parties on a non-contingent basis with prior written notice of no less than thirty (30) calendar days. The independent auditor will be subject to appropriate security restrictions and will be required to agree to confidentiality terms acceptable to Aegis. The Parties will mutually agree on the scope and timing of the audit and the audit will be conducted during Aegis’ regular business hours. Customer will be responsible for any fees charged by the independent auditor to execute the audit and Customer shall be fully liable for the actions and omissions of its personnel and the independent auditor while on Aegis’ premises and/or completing the audit. Any audit shall not involve: (i) access to Aegis’ systems or applications; (ii) installation or use of any audit software; (iii) access to any highly sensitive areas; or (iv) access to a third party’s information. In no event shall Aegis be required to divulge any information or provide access to any sites, applications, or systems that would result in a breach of any of its legal or contractual obligations (including any agreements with its partners, licensors, or any other third parties), or which would result in a waiver of legal privilege. Further, Aegis shall not be required to disclose its internal cost information or documentation of proprietary business practices. All summaries and information divulged pursuant to this Section 9.1 shall be considered Aegis Confidential Information, and Aegis shall be entitled to redact (or withhold) any information that does not relate to Customer or Customer Personal Data, or would compromise or threaten to compromise the security of Aegis’ Offerings.
9.2 Customer shall be permitted to take appropriate action to promptly remediate any unauthorized use of Customer Personal Data or other breach of this DPA, such as suspension of sharing Customer Personal Data or termination of the Agreement. Notwithstanding the foregoing, Aegis shall retain exclusive control of any technical steps to be taken.
10. INTERNATIONAL DATA TRANSFERS
10.1 Subject to this Section 10, Customer acknowledges that Aegis may transfer and process Customer Personal Data to and in the U.S. and anywhere else Aegis maintains data processing operations. Aegis will ensure such transfers are made in compliance with Data Protection Laws and this Section 10.
10.2 Where Customer (data exporter) transfers Customer Personal Data relating to Individuals located in the EU/EEA from the EU/EEA to Aegis (data importer) outside the EU/EEA, such transfers will be conducted in accordance with this DPA and the provisions contained in module 2 (controller-to-processor) of standard contractual clauses adopted by the European Commission in its Implementing Decision (EU) 2021/914 of 4 June 2021 (the “EU SCCs”), available at: https://eur-lex.europa.eu/eli/dec_impl/2021/914/oj?uri=CELEX:32021D0914&locale=en. The EU SCCs are incorporated herein by reference and will be considered duly executed between the Parties upon entering into this DPA subject to the following details:
10.2.1 Clause 7 (Docking Clause) will not apply.
10.2.2 General written authorization is elected for Clause 9 (Use of Sub-processors) and the requirements are set out in Section 3 of this DPA.
10.2.3 The optional language in Clause 11 (Redress) will not apply.
10.2.4 The supervisory authority for Clause 13 (Supervision) is Ireland’s Data Protection Commission.
10.2.5 In Clause 17 (Governing Law), option 1 shall apply. The Parties agree that the clauses shall be governed by the law of Ireland.
10.2.6 The choice of forum and jurisdiction for Clause 18 (Choice of Forum and Jurisdiction) shall be the courts of Ireland.
10.2.7 Annex I is completed with the information set forth in Attachment 1 to this DPA.
10.2.8 The description of the Technical and Organizational Security Measures implemented by the Data Importer (Annex II) is set forth in Attachment 2 to this DPA.
10.3 Where Customer (data exporter) transfers Customer Personal Data relating to Individuals residing in the UK from the UK to Aegis (data importer) outside the UK, the international data transfer addendum issued by the UK Information Commissioner’s Office under S119A(1) of the Data Protection Act 2018 (“UK Data Transfer Addendum”), available at https://ico.org.uk/media/for-organisations/documents/4019539/international-data-transfer-addendum.pdf, shall apply. The UK Data Transfer Addendum is incorporated herein by reference and will be considered duly executed between the Parties upon entering into this DPA subject to the following details:
10.3.1 The details of the Parties in Table 1 are set out in Attachment 1 to this DPA.
10.3.2 The selected module and clauses in Table 2 are set out in Section 10.2 of this DPA.
10.3.3 The appendix information in Table 3 is set out in Attachment 1 to this DPA.
10.3.4 Exporter is selected in Table 4.
10.4 To the extent that a court of competent jurisdiction or data protection authority orders that the measures described in this Section 10 cannot be relied on to transfer Personal Data (within the meaning of Data Protection Laws), Aegis may implement any additional measures or safeguards that may be reasonably required to lawfully support the transfer of the Customer Personal Data.
ATTACHMENT 1
The following chart describes the processing activities Aegis will perform to provide the Offerings:
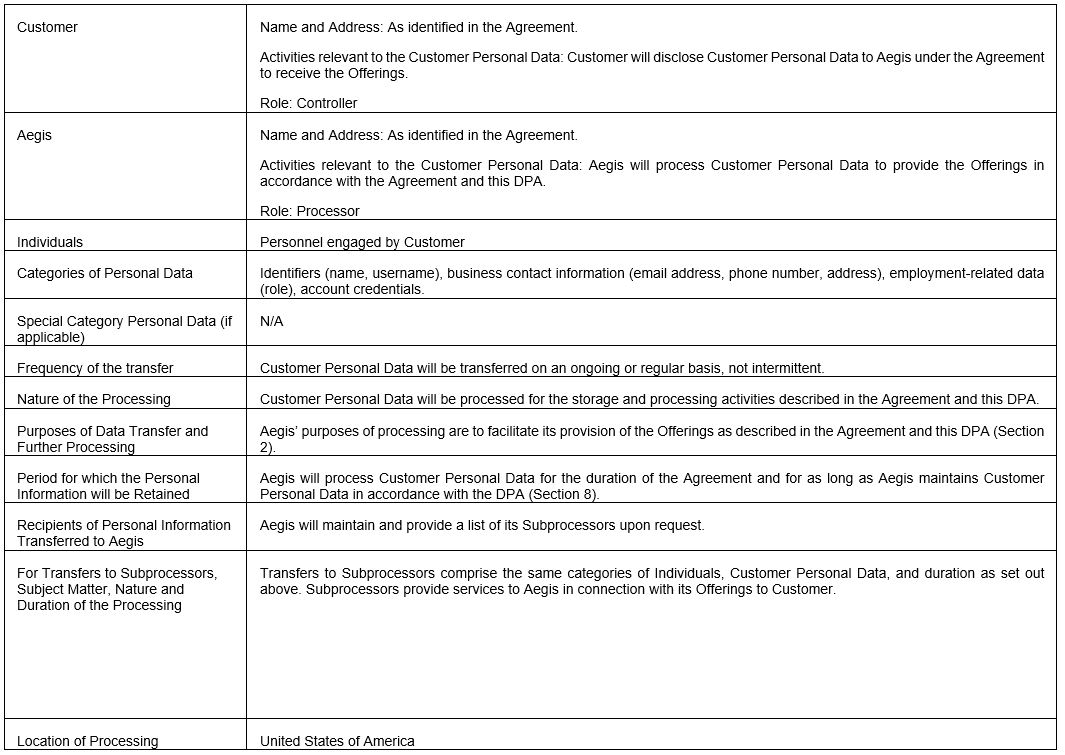
ATTACHMENT 2
INFORMATION SECURITY REQUIREMENTS
This Information Security Requirements Attachment (the “ISRs”) sets forth the minimum standards for protection of Customer Data by Aegis. Any capitalized terms not defined in these ISRs shall have the meaning set forth in the Agreement or the DPA.
1.0 DEFINITIONS.
1.1 "Aegis Systems” means all applications, operating systems, databases, devices, and servers controlled by Aegis and used in connection with the Offerings.
1.2 “Customer Data” means Customer Personal Data and design data, process data, part lists, product lists, production flows, process trace data, and computer-aided design files processed by Aegis under the Agreement.
1.3 “Customer Systems” means all Customer applications, operating systems, databases, servers, and devices accessed by Aegis in connection with the Offerings.
1.4 “Information Security Standards” means: (i) standards prescribed for general use by the National Institute of Standards and Technology or the International Organization for Standardization and International Electro-technical Commission 27000 series; or (ii) a field-specific legal or internationally recognized standard, but only to the extent data is exclusively covered by such standard.
1.5 “Aegis Personnel” means all personnel resources engaged by or on behalf of Aegis who perform the Offerings, e.g., employees and other authorized representatives of Aegis and/or Subprocessors.
2.0 SECURITY PROGRAM
2.1 Aegis shall employ commercially reasonable physical, administrative, and technical security controls designed to protect Customer Data in its possession that are appropriately tailored to the sensitivity of the Customer Data. Such controls shall in no instance be less protective than the strictest procedures used to secure and retain the confidentiality of Aegis’ own information of a like kind and in all instances must conform to industry standards and Data Protection Laws.
2.2 Aegis shall have in place a written information security program that meets the requirements of Data Protection Laws and the requirements set forth in these ISRs. Aegis shall review and, if needed, update, the written information security program at least annually and whenever there is a material change that affects Aegis’ security program.
2.3 The Aegis Practices and Systems Supporting Customer Data Security, Cyber Security, and Legal Compliance Policy (the “Policy”) outlines the systems, architecture, and processes Aegis employs with respect to the Offerings. Customer may request a copy of the most recent version of the Policy at any time during the term of the Agreement. The Policy is provided for informational purposes only and does not form part of these ISRs, the DPA, or the Agreement. The terms and conditions of these ISRs govern Aegis’ security obligations and the Policy shall not create any binding obligations on Aegis. The Policy is current as of the date indicated on the Policy. Aegis reserves the right to update or modify the Policy in its sole discretion without notice.
3.0 AEGIS PERSONNEL
3.1 Aegis shall ensure that all Aegis Personnel receive appropriate security awareness education and training, including regular updates to organizational policies, procedures, and standards, as is relevant to their job function.
3.2 Prior to granting access to Customer Data to any Aegis Personnel, Aegis shall ensure that such Aegis Personnel have (i) signed the appropriate non-disclosure or confidentially agreement if and to the extent required by the Agreement; and (iii) agreed to abide by Aegis’ written information security program.
4.0 ACCESS TO CUSTOMER SYSTEMS
Where Aegis is granted access privileges to Customer Systems, Aegis will ensure that only Aegis Personnel that are authorized by Aegis to perform the Offerings (“Authorized Aegis Personnel”) have access to the Customer Systems. Aegis will protect and keep confidential Customer Systems access credentials (“Credentials”), including by ensuring that such Credentials are not stored or transmitted in an unsecure manner. Aegis will have and enforce a policy prohibiting its Authorized Aegis Personnel from sharing any Credentials with any other person, including with any other individual (whether authorized or not), or to permit any other person to log on as such Authorized Aegis Personnel. Aegis will ensure that the Customer Systems, including all Credentials, will be used by Authorized Aegis Personnel solely for the limited purpose authorized by Customer in the Agreement, and not for any personal use or any other purposes.
5.0 ACCESS CONTROLS
5.1 For Aegis Systems that store Customer Data, Aegis shall:
5.1.1 Enforce a ‘least privilege’ model to complete a task or duty.
5.1.2 Restrict access on a need-to-know basis and only grant access to information that Aegis Personnel need to perform their tasks.
5.1.3 Segregate roles for access request, access authorization, and access administration and have requirements for formal authorization of access requests and for periodic review of access controls with appropriate and timely remediation and of any finding resulting from the periodic review.
5.1.4 Assign unique user IDs to each user and require that all Aegis Personnel keep all authentication information confidential and ensure it is not disclosed to anyone.
5.1.5 Promptly revoke Aegis Personnel access upon the end of employment with Aegis, the end of the Agreement, or when such access is no longer necessary to provide the Offerings (whichever occurs first).
5.1.6 Conduct regular reviews of Aegis Personnel access to Aegis Systems to confirm that the requirements of this Section 5 are being met.
5.2 For Aegis Systems that store Customer Data, Aegis will require successful completion of multi-factor authentication (MFA) to access such system.
6.0 CLOUD SYSTEMS
6.1 With respect to cloud-based environments that use a “shared responsibility” model or similar framework (such as Amazon Web Services or Microsoft Azure), Aegis shall comply with all responsibilities under such model or framework.
7.0 MONITORING
7.1 Aegis shall have in place appropriate firewall technologies consistent with generally accepted industry standards to protect Aegis Systems that store Customer Data, and such firewall technologies shall be kept current with the most recent updates. Aegis shall ensure the firewalls only have necessary services and ports open to Aegis. Aegis will update network and web application firewalls regularly with updated threat and technique-based signatures and intelligence.
7.2 Aegis shall ensure that there is current anti-virus/anti-malware software running on Aegis Systems that store Customer Data, and that such software is kept current with the most recent updates consistent with generally accepted industry standards.
7.3 Aegis shall patch all Aegis Systems that store Customer Data with all manufacturer-recommended patches and updates according to a schedule based on the criticality of each patch and/or update.
7.4 Aegis will implement reasonable monitoring and logging controls that meet or exceed Information Security Standards and that identify security issues in near real-time for Aegis Systems that store Customer Data.
7.5 Aegis will conduct routine network and host scans on a regular basis for systems that store Customer Data and shall promptly remediate any identified vulnerabilities at its expense.
8.0 STORAGE AND TRANSMISSION
8.1 Aegis shall encrypt all Customer Data at rest on Aegis Systems. Aegis shall also encrypt Customer Data that is in transit, moving over wired and wireless local and/or wide area networks and the internet, using Transport Layer Security (TLS). Aegis shall not place Customer Data on systems or locations used for development or testing unless necessary to provide the Offerings.
8.2 Aegis shall use appropriate, up-to-date, and secure key management procedures consistent with generally accepted industry standards.
8.3 Aegis shall have, maintain, and enforce a policy that prohibits the transfer of Customer Data to any device not owned or controlled by Aegis.
8.4 If Aegis stores any Customer Data on digital or electronic portable storage devices such as computer laptops, smart phones, CDs, diskettes, portable drives, magnetic tapes and other similar devices, Aegis will encrypt such Customer Data using 256-bit or higher encryption and will take such other steps to protect such stored Customer Data from unauthorized use, loss or disclosure. Such storage will only be used when absolutely necessary, and only to the limited extent necessary, to provide the Offerings and will only continue for as long as necessary to provide the Offerings. Such Customer Data will be securely and permanently removed by Aegis from any and all such storage media promptly thereafter.
8.5 Aegis Personnel who access Customer Data on Aegis Systems must be required to use an Aegis-provided laptop, or, if using a personal/privately-owned computer, then access must be through a virtual desktop interface (VDI) that prevents storage, interception, or manipulation of information on privately owned equipment.
9.0 ASSET MANAGEMENT
9.1 Aegis shall maintain custody of media containing Customer Data in transport except when transported by a reputable courier with tracking.
9.2 If Aegis uses removable media for Customer Data, Aegis shall maintain an inventory system for such media.
9.3 When disposing of media that contained Customer Data, Aegis must sanitize the media in accordance with Information Security Standards, including NIST SP800-88 Rev 1, Guidelines for Media Sanitization. If sanitization is not possible, Aegis shall securely destroy the media.
10.0 PHYSICAL SECURITY
10.1 Aegis shall restrict access to, control, and monitor all physical areas in Aegis’ premises that store Customer Data, including areas where services are performed in which Aegis Personnel have access to Customer Data, or Aegis Systems that store Customer Data.
10.2 Aegis shall restrict access to paper-based records containing Customer Data by securing such records in locked facilities or containers and only allowing access to those Aegis Personnel with a business need.
10.3 Aegis premises are alarmed and monitored to prevent unauthorized access. All Aegis Systems with access to Customer Data are secured in locked rooms. Access to these rooms is limited to Aegis Personnel.
10.4 Aegis shall ensure all printed records that contain Customer Data are securely destroyed by shredding.




